Azure Sentinel and the Art of Cyber Deception: Project Honeypot

Today's post skims the surface of cloud technology and cybersecurity with a small lab setting up a honeypot. This project provided me with an insightful, hands-on journey, and I'm excited to share some of the setup and results.
Understanding Azure Sentinel
First and foremost, a primer on Azure Sentinel. This cloud-native SIEM (Security Information and Event Management) tool from Microsoft is the backbone of the modern security operation center. As digital threats evolve and increase in sophistication, tools like Azure Sentinel play an invaluable role by offering advanced threat detection, automatic security responses, and the capability to manage security across different cloud environments.
The Core Objective
My central goal was integrating Azure Sentinel with a decoy virtual machine, effectively creating a honeypot. Honeypots are purposely vulnerable systems that act as lures for potential cyber adversaries, allowing us to monitor and learn from their actions without any real-world consequences.
Setting up the Stage
To get started, I provisioned a VM within Azure and intentionally kept some security features relaxed. This would make the system appear as a low-hanging fruit for attackers. I then integrated this VM with Azure Sentinel to capture logs and events. To ensure a more realistic environment, I exposed the Remote Desktop Protocol (RDP) service, which is notoriously targeted for brute-force attacks. With everything set, the stage was primed for potential attackers.
When Threats Became Reality
Soon after setting up the honeypot, the expected started happening. Malicious attempts poured in from different corners of the globe. What was striking was the concentration of these attempts. It's intriguing to see the varying degrees of activity from different countries. Vietnam, for instance, had a substantially higher volume of attempts than the other nations. It serves as a vivid reminder that threats can emerge from any corner of the world, and the origin of these threats can sometimes surprise us.
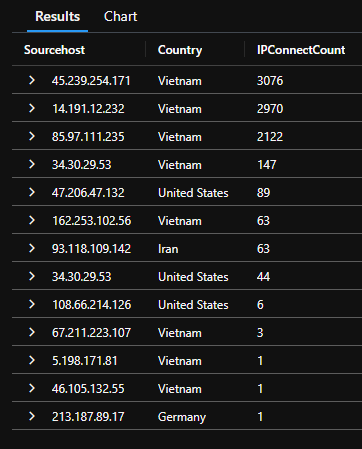
Tracing the Digital Footprints
Now, to add a layer of intrigue, Using a custom PowerShell script, I mined the logs to extract the IP addresses of the attackers. I then mapped these IP addresses to their geolocations, creating a snapshot of global malicious activities. This not only gave me a geographical representation but also a deeper insight into the persistence and spread of these attacks.
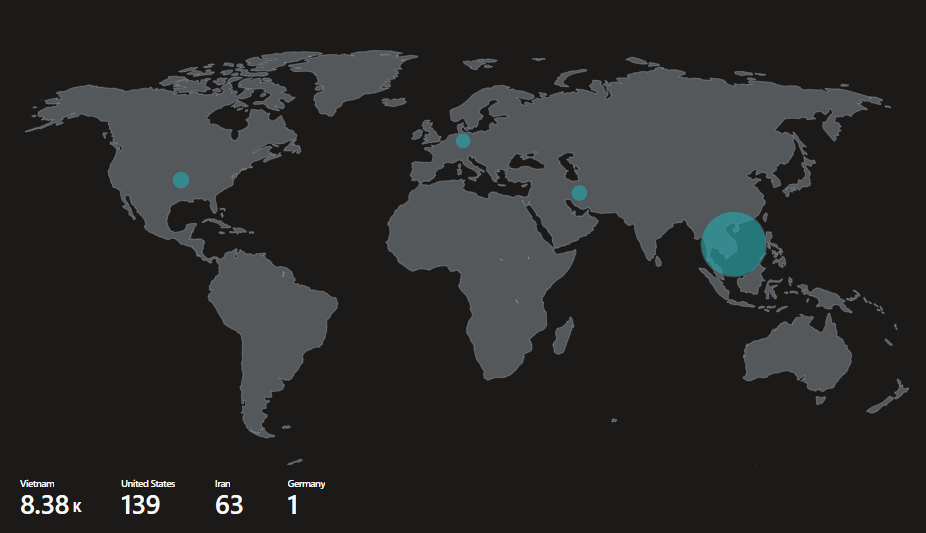
Concluding Thoughts and Reflections
Setting up this honeypot with Azure Sentinel reaffirmed the importance of proactive cybersecurity measures. The real-time visuals, combined with the analytical capabilities of Azure, emphasized the constant and evolving nature of digital threats. While the project was technically focused, it also inspired some philosophical musings. In the vast digital expanse, our systems, no matter how inconspicuous, are always under the gaze of those with malicious intent. The speed at which this VM was found surprised me; just 30 minutes after going live, the first login attempt was made. I may do another iteration of this honeypot lab with more sophistication and running on my ProxMox home lab environment!
I look forward to your thoughts, feedback, and any exciting revelations you've had in your cyber endeavors.
