Hashing It Out: File Integrity Monitor with PowerShell

In the realm of cybersecurity, there are foundational principles that govern our approach to safeguarding digital assets. One of these fundamental guidelines is the CIA triad – an acronym representing the three essential pillars of security: Confidentiality, Integrity, and Availability. While each component is critical in its own right, for this project, I centered my focus on Integrity.
Integrity refers to the assurance that data remains consistent, accurate, and unaltered without appropriate authorization. In simpler terms, it's the guarantee that the information you retrieve has not been tampered with since it was created, transmitted, or stored.
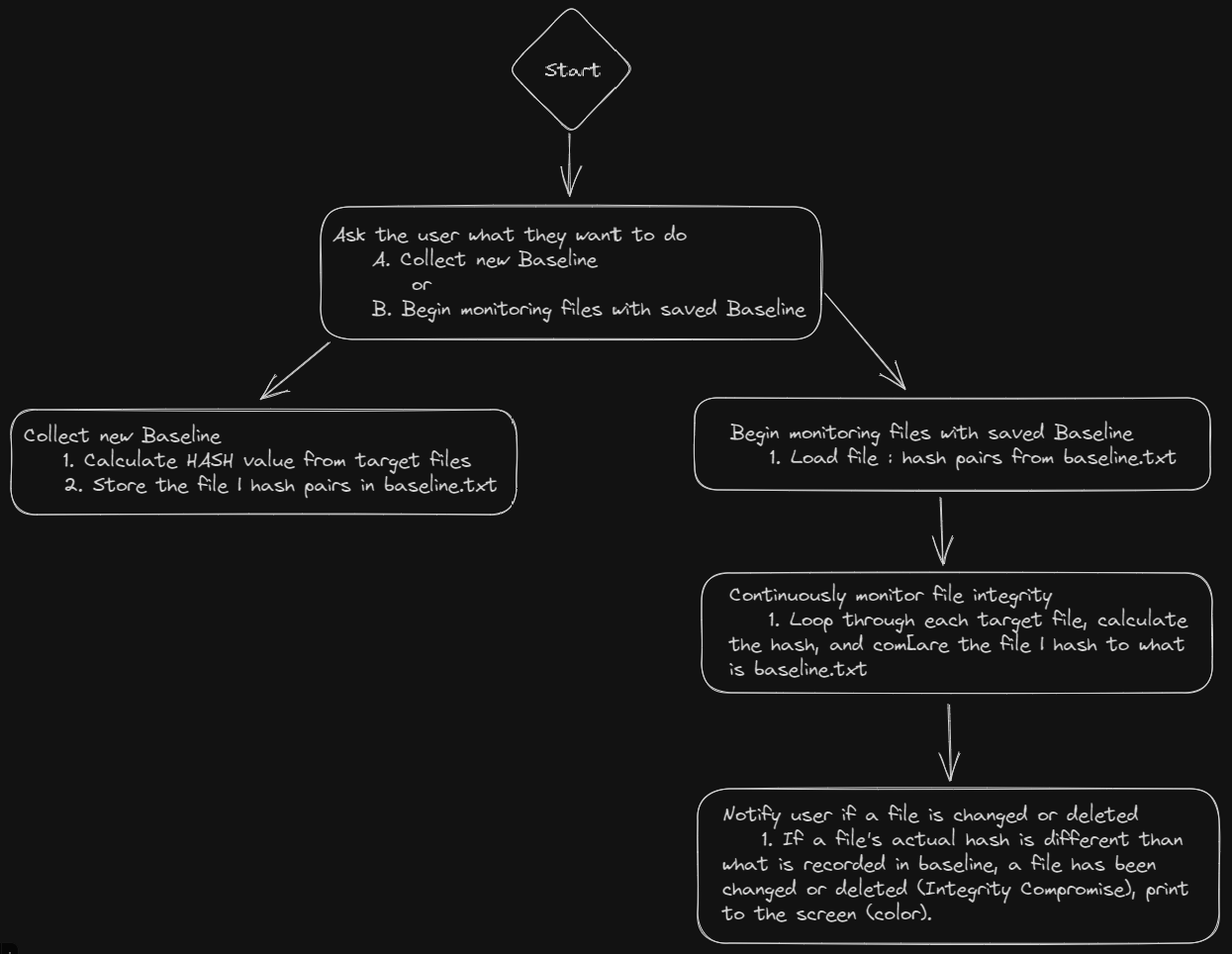
The File Integrity Monitor I developed is a testament to the importance of data integrity. Let's dive deeper into its working:
- Option A: The program first establishes a baseline by hashing the files in a target folder and saving these hashes in a file named
baseline.txt. This step sets a trusted standard against which future checks can be compared.
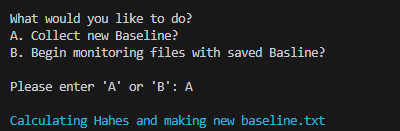
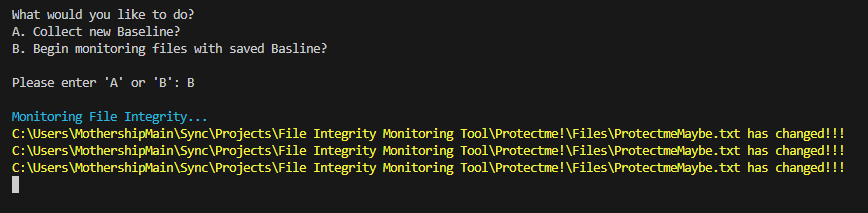
- Option B: With the baseline set, the program enters a monitoring phase. In this mode, the program continuously hashes the files in the target folder and compares these new hashes against those saved in the
baseline.txt. If discrepancies arise – which could suggest modifications, deletions, or the introduction of new files – the program alerts the user. Alerts are designed to be immediately noticeable with color-coded text for various events: red for file modifications, yellow for file deletions, and green for newly created files.
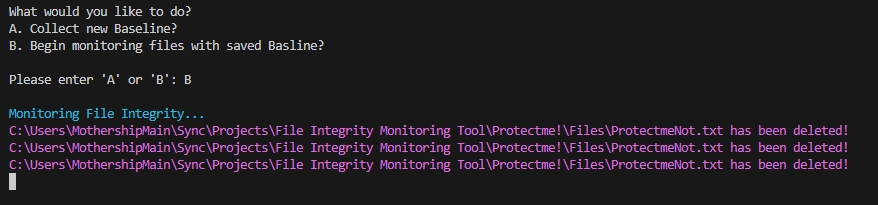
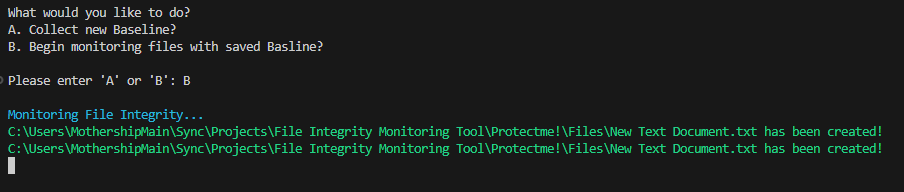
In the vast and complex world of business, ensuring the integrity of data is an imperative, not just a choice. Picture a large enterprise: financial statements shaping critical decisions, client contracts anchoring trust, and proprietary code fueling innovation. Any unauthorized tweak or tamper to these files can spiral into grave operational, financial, and reputational pitfalls.
A tool like the File Integrity Monitor steps in here, acting as a vigilant sentinel. It doesn't just detect changes; it empowers businesses to act quickly, ensuring that their foundational data remains untouched and trustworthy. In essence, while my PowerShell-based monitor might be deemed simple, its role is profoundly significant. You can find the original PowerShell script along with the files I used on my GitHub.
In the labyrinth of cybersecurity tools and strategies, sometimes, it's the basic, clear-cut solutions like this that resonate the loudest, ensuring that our core data remains just as it should be: pristine and uncompromised.
