Hidden Flaws in Unix Printing System

In the shadowy corners of the internet, a new vulnerability has emerged—one that doesn't attack through flashy ransomware or phishing emails but through the humble act of printing. Security researcher Simone Margaritelli (@evilsocket) has uncovered a series of critical flaws in the Common Unix Printing System (CUPS) that could allow attackers to seize control of Unix systems remotely. Find his write-up HERE to get to the source of this information.
The Silent Intrusion: What Happened?
The vulnerabilities reside in cups-browsed, a component of CUPS responsible for printer discovery and management. Here's how the flaws break down:
- CVE-2024-47176: In versions up to 2.0.1,
cups-browsedlistens on UDP port 631—the Internet Printing Protocol (IPP)—and naively trusts any incoming packets. This allows attackers to trigger printer requests from malicious URLs. - CVE-2024-47076:
libcupsfiltersup to version 2.1b1 fails to properly sanitize IPP attributes, allowing unchecked data to infiltrate the CUPS system. - CVE-2024-47175: Similarly,
libppdup to version 2.1b1 doesn't validate IPP attributes, enabling attackers to inject harmful data into printer configuration files. - CVE-2024-47177: The
foomatic-ripfilter incups-filtersup to version 2.0.1 permits arbitrary command execution through specially crafted PostScript Printer Description (PPD) files.
Collectively, these vulnerabilities allow an attacker to send malformed UDP packets to a target system running CUPS. The attacker can then replace or add malicious printer configurations, triggering code execution when a print job starts. The affected platforms aren't limited to a niche segment—they span numerous GNU/Linux distributions, several BSD variants, and potentially other Unix-like systems like Oracle Solaris and ChromeOS.
The Ripple Effect: Understanding the Impact
The attack vector is deceptively simple yet alarmingly effective:
- Remote Code Execution: An attacker sends a malicious UDP packet to port 631, tricking the system into making an IPP request to a rogue URL under the attacker's control.
- Unseen Entry Points: The threat isn't confined to external attacks from the internet. Within local networks, attackers can spoof zero-configuration networking (zeroconf) or Multicast DNS (mDNS) advertisements to exploit the same vulnerabilities.
- Wide-Scale Exposure: Systems with
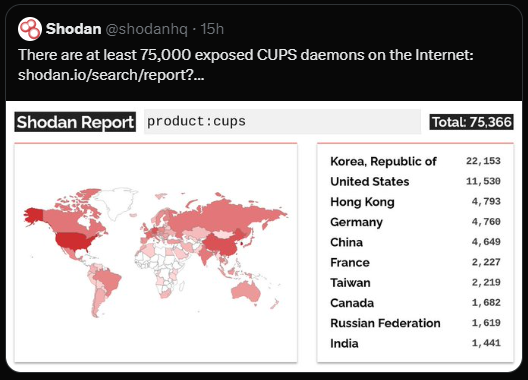
cups-browsedenabled—the default in many distributions—are vulnerable. Security scans have identified hundreds of thousands of such systems online, each a potential victim.
Why This Matters: The Hidden Dangers
CUPS is ubiquitous in the Unix world, silently running in the background of servers, desktops, and even IoT devices. Its pervasiveness makes this vulnerability particularly dangerous for several reasons:
- Stealthy Persistence: Once attackers control the printer configuration, they can maintain persistence by exploiting how printer attributes are handled. Unsanitized attributes are written into PPD files, which can include commands executed during the printing process, leading to a full system compromise.
- Default Vulnerability: Many users are unaware that
cups-browsedis enabled by default, leaving them exposed without any overt signs of danger. - Cross-Platform Risk: The issue isn't isolated to a single operating system or environment, making the potential impact widespread and diverse.
Shields Up: How to Protect Your Systems
1. Disable cups-browsed
If network printer discovery isn't a necessity—which it often isn't for individual users—the most straightforward solution is to disable the cups-browsed service.
sudo systemctl disable cups-browsed
sudo systemctl stop cups-browsed
2. Update Your System
Ensure that all CUPS-related packages are updated to the latest versions where these vulnerabilities are patched. Regularly check for updates through your distribution's package manager.
3. Block Vulnerable Ports
If disabling cups-browsed isn't feasible, consider blocking incoming traffic on UDP port 631. Additionally, blocking DNS Service Discovery traffic can prevent local network attacks via zeroconf and mDNS.
sudo ufw deny 631/udp
sudo ufw deny mdns
4. Remove Unnecessary Services
For those who don't require any printing services, removing CUPS and related zeroconf services like Avahi or Bonjour can further reduce the attack surface.
Beneath the Surface: A Deeper Look into the Exploit
At the heart of this vulnerability is a fundamental breach of trust within the CUPS system:
- Untrusted Inputs:
cups-browsedaccepts IPP requests without proper validation. Attackers exploit this by injecting malicious URLs into the system. - Malicious PPD Files: By feeding unvalidated IPP attributes into PPD files, attackers can insert commands that execute during the printing process via the
foomatic-ripfilter. - Command Execution: These commands run with the privileges of the printing system, which can be elevated, allowing attackers to gain significant control over the target machine.
The elegance of this exploit lies in its subtlety. It doesn't rely on social engineering or user interaction; instead, it manipulates the system's trusted processes.
Key Takeaways:
- Critical Vulnerabilities in CUPS: Multiple flaws allow remote code execution through unsanitized IPP attributes and improper handling of printer configurations.
- Immediate Actions:
- Disable
cups-browsedif it's not necessary for your operations. - Update CUPS and Related Packages to versions where the vulnerabilities are patched.
- Block UDP Port 631 and consider removing unnecessary services like Avahi and Bonjour.
- Disable
- Stay Vigilant: Regularly review and update your system's security measures to protect against emerging threats.
Even the most unassuming services can become gateways for cyberattacks in the digital age. Don't let the printer in the corner of your office be the Achilles' heel of your security infrastructure.
