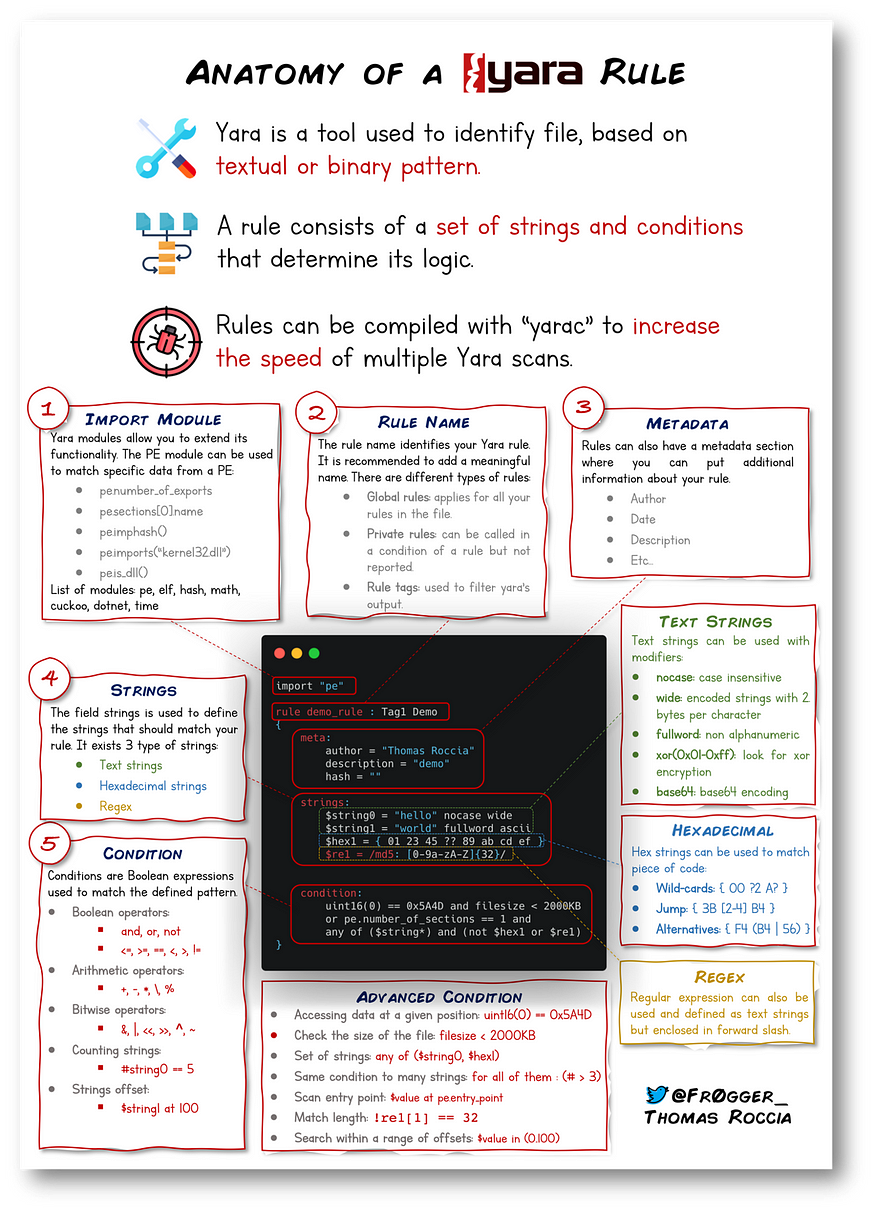
Unraveling YARA: Creating and Understanding Rules

In the realm of cybersecurity, YARA stands as a robust tool, coined as "The pattern matching swiss knife for malware researchers (and everyone else)" (Virustotal., 2020). Its potent capabilities for identifying and labeling patterns within both binary and textual data have made it a mainstay for many security experts.
YARA's Working Mechanism
YARA operates on the foundational element of strings, identifying distinct patterns within files to ascertain their characteristics—often to uncover malicious files from benign ones. The power lies in the user’s hands, as YARA’s syntax, while straightforward, demands a deep understanding of the search patterns to construct efficient and effective rules.
A YARA command necessitates two arguments to function:
- The rule file created.
- The name of the file, directory, or process ID for rule application.
Lets get a little deeper into this!
Crafting Our First YARA Rule
Embarking on the YARA journey, let’s construct our first rule. Create a file named helloyara and a rule file myfirstrule.yar with the following within our rule.
rule examplerule {
condition: true
}
Execute the rule against helloyara with the command:
yara myfirstrule.yar somefile
If our rule is true, we should expect the output: examplerule helloyara
If our rule is false, error scanning sometextfile: could not open file
Diving Deeper: Metadata, Strings, and Conditions
In YARA:
- Meta: This section holds descriptive information, similar to comments in code, aiding in summarizing the rule for user understanding.
- Strings: Employs strings for searching specific text or hexadecimal patterns within files.
- Conditions: Specifies the conditions under which the rule is considered a match.
Below is an elementary example to check for the presence of the “Hello Yara” string:
rule helloyara_checker{
strings:
$helloyara = "Hello Yara!"
condition:
$helloyara
}
This basic rule is designed to verify the presence of the specific string "Hello Yara!" within a file. As it stands, this rule is literal and will not recognize variations in letter casing. To identify this string in upper and lower case letters, we can employ the condition any of them
rule helloyara_checker{
strings:
$helloyara = "Hello Yara!"
$helloyara_lowercase = "hello yara"
$helloyara_uppercase = "HELLO YARA"
condition:
any of them
}
This adjustment now triggers the rule for files containing any of the three string variations.
Employing Operators
YARA allows the utilization of operators (<=, >=, !=) within conditions, as illustrated below:
rule helloyara_checker{
strings:
$hello_yara = "Hello Yara!"
condition:
#hello_yara <= 10
}
Here, the rule matches only if “Hello Yara!” appears ten or fewer times.
Augmenting with Combined Keywords
Expand the rule's efficiency by combining multiple conditions:
rule helloyara_checker{
strings:
$helloyara = "Hello Yara!"
condition:
$helloyara and filesize < 10KB
}
In this instance, the rule searches for “Hello Yara!” in files smaller than 10KB.
Beyond the Basics
This overview offers just a glimpse into YARA’s extensive capabilities. In upcoming posts, I will introduce and demo third-party tools such as LOKI and THOR and get some malware analysis into the mix. By utilizing malware analysis to gather Indicators of Compromise (IOCs), we can develop and do live testing of YARA rules in a malware lab or sandbox environment based on those IOC's. This multifaceted approach amplifies our capacity to understand and mitigate malware threats and use YARA in a way it was truly meant to be deployed.
Eager to delve further? An excellent additional read would be the YARA documentation, which provides extensive insights into writing rules (YARA Documentation). Also give a look at the GitHub repo Awesome YARA which has even more resources along with shared rules based on IOCs.
As we conclude this introductory post, remember that this is just the beginning. The exploration into YARA and its powerful capabilities will continue, aiding in our persistent quest for robust cybersecurity mechanisms. Stay tuned for more!
